Learning Objectives
- Explain the history of computer-mediated communication.
- Differentiate between synchronous and asynchronous communication.
- Explain netiquette.
- Describe online impression formation.
- Describe the absence of nonverbal cues in online communication.
Interpersonal Communication in Mediated Contexts
In today’s world, we all spend a lot of time on various devices designed to make our lives easier. From smartphones to social media, we are all in constant contact with family, friends, coworkers, etc. Since the earliest days of communication technologies, we have always used these technologies to interact with one another. This chapter will examine how technology mediates our interpersonal relationships.

Allowing People to Communicate
The early Internet was not exactly designed for your average user, so it took quite a bit of skill and “know how” to use the Internet and find information. Of course, while the Internet was developing, so was its capability for allowing people to communicate and interact with one another. In 1971, Ray Tomlinson sent a message from one computer to another computer sitting right next to it, sending the message through ARPANET and creating the first electronic email. In addition to email, another breakthrough in computer-mediated communication was the development of Internet forums or message/bulletin boards, which are online discussion sites where people can hold conversations in the form of posted messages. As you can see, from the earliest days of the Internet, people were using the Internet as a tool to communicate and interact with people who had similar interests. Today, there are hundreds of ways to connect with others in an online environment.
Synchronous and Asynchronous Communication
Synchronous communication happens in real time, like having a class discussion in a face-to-face setting or talking to a someone after class. But you can communicate synchronously in an online environment too, through the use of tools like online chat; Internet voice of video calling systems like Skype or Google Hang-outs; or through the use of web-based video conferencing software like WebEx, Zoom, or Collaborate. Another popular form of synchronous online communication is gaming. For example, in Figure 12.5, Sam and Pat are in some kind of underworld, fiery landscape. Pat is playing a witch character, and Sam is playing a vampire character. The two can coordinate their movements to accomplish in-game tasks because they can talk freely to one another while playing the game in real time.

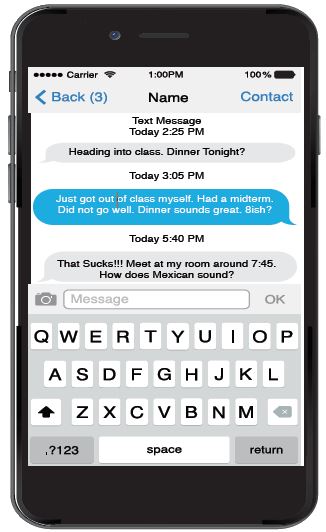
Conversely, asynchronous communication is the exchange of messages with a time lag. In other words, in asynchronous communication, people can communicate on their own schedules as time permits instead of in real time. For example, Figure 12.6 shows a conversation between two college students. In this case, two college students are using SMS, commonly called texting) to interact with each other. The conversation starts at 2:25 PM. The first person initiates the conversation but doesn’t get a response until 3:05 PM. The third turn in the interaction then doesn’t happen until 5:40 PM. In this exchange, the two people interacting can send responses at their convenience, which is one of the main reasons people often rely on asynchronous communication. Other common forms of asynchronous communication include emails, instant messaging, and online discussions.
Netiquette
Over the years, numerous norms have developed to help individuals communicate in the CMC context. They’re so common that we have a term for them, netiquette. Netiquette is the set of professional and social rules and norms that are considered acceptable and polite when interacting with another person(s) through mediating technologies. Let’s break down this definition.
Contexts
First, our definition of netiquette emphasizes that different contexts can create different netiquette needs. Specifically, how one communicates professionally and how one communicates socially are often quite different. For example, you may find it entirely appropriate to say, “What’s up?!” at the beginning of an email to a friend, but you would not find it appropriate to start an email to your boss in this same fashion. Furthermore, it may be entirely appropriate to downplay or disregard spelling errors or grammatical problems in a text you send to a friend, but it is completely inappropriate to have those same errors and problems in a text sent to a professional-client or coworker. One of the biggest challenges many employers have with young employees who are fresh out of college is that they don’t know how to differentiate between appropriate and inappropriate communicative behavior in differing contexts. This lack of professionalism is also a problem commonly discussed by college and university faculty and staff. Think about the last email you sent to one of your professors? Was this email professional? Did you remember to sign your name? You’d be amazed at the lack of professionalism many college and university faculty and staff see in the emails sent by your peers.
Here are some general guidelines for sending professional emails:
• Include a concise, direct subject line.
• Do not mark something as “urgent” unless it really is.
• Begin with a proper greeting (Dear Mr. X, Professor Y:, etc.)
• Double-check your grammar.
• Correct any spelling mistakes.
• Include only essential information. Be concise.
• State your intention clearly and directly.
• Make sure your message is logically organized.
• Be polite and ensure your tone is appropriate.
• Avoid all CAPS or all lowercase letters.
• Avoid “textspeak” (e.g., plz, lol)
• If you want the recipient to do something, make the desired action very clear.
• End with a polite closing (using “please” and “thank you”).
• Do not send an email if you’re angry or upset.
• Edit and proofread before hitting “send.”
• Use “Reply All” selectively (very selectively)
Rules and Norms
Second, our definition of netiquette combines both rules and norms. Part of being a competent communicator in a CMC environment is knowing what the rules are and respecting them. For example, if you know that Twitter’s rules ban hate speech, then engaging in hate speech using the Twitter platform shows a disregard for the rules and would not be considered appropriate behavior. In essence, hate speech is anti-netiquette. We also do not want to ignore the fact that in different CMC contexts, different norms often develop. For example, maybe you’re taking an online course and you’re required to engage in weekly discussions. One common norm in an online class is to check the previous replies to a post before posting your reply. If you don’t, then you are jumping into a conversation that’s already occurred and throwing your two-cents in without knowing what’s happening.
Acceptable and Polite CMC Behavior
Third, netiquette attempts to govern what is both acceptable and polite. Yelling via a text message may be
acceptable to some of your friends, but is it polite given that typing in all caps is generally seen as yelling?
Being polite shows others respect and demonstrates socially appropriate behaviors.
If you’ve spent any time online recently, you may have noticed that it can definitely feel like a cesspool. There are many trolls, making the Internet a place where civil interactions are hard to come by. Mitch Abblett came up with five specific guidelines for interacting with others online:
1. Be kind and compassionately courteous with all posts and comments.
2. No hate speech, bullying, derogatory or biased comments regarding self, others in the community, or others in general.
3. No Promotions or Spam.
4. Do not give mental health advice.
5. Respect everyone’s privacy and be thoughtful in the nature and depth of your sharing.14
Think about your interactions with others in the online world. Have you ever communicated with others without considering whether your own intentions and attitude are appropriate?
Online Interaction
Fourth, our definition involves interacting with others. This interaction can be one-on-one, or this interaction can be one-to-many. The first category, one-on-one, is more in the wheelhouse of interpersonal communication. Examples include sending a text to one person, sending an email to one person, talking to one person via Skype or Zoom, etc. The second category, one-to-many, requires its own set of rules and norms. Some examples of common one-to-many CMC could include engaging in a group chat via texting, “replying all” to an email received, being interviewed by a committee via Skype, etc. Notice that our examples for one-to-many involve the same technologies used for one-on-one communication. However, the norms may be different for each.
Range of Mediating Technologies
Lastly, netiquette can vary based on the different types of mediating technologies. For example, it may be considered entirely appropriate for you to scream, yell, and curse when your playing with your best friend on Fortnite, but it wouldn’t be appropriate to use the same communicative behaviors when engaging in a video conference over Skype. Both technologies use VoIP, but the platforms and the contexts are very different, so they call for different types of communicative behaviors. Some differences will exist in netiquette based on whether you’re in an entirely text-based medium (e.g., email, texting) or one where people can see you (e.g., Skype, WebEx, Zoom). Ultimately, engaging in netiquette requires you to learn what is considered acceptable and polite behavior across a range of different technologies.
Online Identity
Online Impression Formation
In the 21st Century, so much of what we do involves interacting with people online. How we present ourselves to others through our online persona (impression formation) is very important. How we communicate via social media and how professional our online persona is can be determining factors in getting a job.
It’s important to understand that in today’s world, anything you put online can be found by someone else. According to the 2018 CareerBuilder.com social recruiting survey, a survey of more than 1,000 hiring managers, 70% admit to screening potential employees using social media, and 66% use search engines to look up potential employees. In fact, having an online persona can be very beneficial. Fortyseven percent of hiring managers admit to not calling a potential employee when the employee does not have an online presence. You may be wondering what employers are looking for when they check out potential employees online. The main things employers look for are information to support someone’s qualifications (58%), whether or not an individual has a professional online persona (50%), to see what others say about the potential candidate (34%), and information that could lead a hiring manager to decide not to hire someone (22%).22 According to CareerBuilder.com, here are the common reasons someone doesn’t get a job because of her/his/their online presence:
• Job candidate posted provocative or inappropriate photographs, videos or information: 40 percent
• Job candidate posted information about their alcohol of drug use: 36 percent
• Job candidate made discriminatory comments related to race, gender, religion, etc.: 31 percent
• Job candidate was linked to criminal behavior: 30 percent
• Job candidate lied about qualifications: 27 percent
• Job candidate had poor communication skills: 27 percent
• Job candidate bad-mouthed their previous company or fellow employee: 25 percent
• Job candidate’s screen name was unprofessional: 22 percent
• Job candidate shared confidential information from previous employers: 20 percent
• Job candidate lied about an absence: 16 percent
• Job candidate posted too frequently: 12 percent23
As you can see, having an online presence is important in the 21st Century. Some people make the mistake of having no social media presence, which can backfire. In today’s social media society, having no online presence can look very strange to hiring managers. You should consider your social media presence as an extension of your resume. At the very least, you should have a profile on LinkedIn, the social networking site most commonly used by corporate recruiters.
Types of Online Identities
Unlike traditional face to face interactions, online interactions can blur identities as people act in ways impossible in face to face interaction. Andrew F. Wood and Matthew J. Smith discussed three different ways that people express their identities online: anonymous, pseudonymous, and real life (Figure 12.9).49

Anonymous Identity
First, people in a CMC context can behave in a way that is completely anonymous. In this case, people in CMC interactions can communicate in a manner that conceals their actual identity. Now, it may be possible for some people to figure out who an anonymous person is (e.g., the NSA, the CIA), but if someone wants to maintain her or his anonymity, it’s usually possible to do so. Think about how many fake Facebook, Twitter, Tinder, and Grindr accounts exist. Some exist to try to persuade you to go to a website (often for illicit purposes like hacking your computer), while others may be “catfishing” for the fun of it.
Catfishing is a deceptive activity perpetrated by Internet predators when they fabricate online identities on social networking sites to lure unsuspecting victims into an emotional/romantic relationship. In the 2010 documentary Catfish, we are introduced to Yaniv “Nev” Schulman, a New York-based photographer, who starts an online relationship with an 8-year-old prodigy named Abby via Facebook. Over the course of nine months, the two exchange more than 1,500 messages, and Abby’s family (mother, father, and sister) also become friends with Nev on Facebook. Throughout the documentary, Nev and his brother Ariel (who is also the documentarian) start noticing inconsistencies in various stories that are being told. Music that was allegedly created by Abby is found to be taken from YouTube. Ariel convinces Nev to continue the relationship knowing that there are inconsistencies and lies just to see how it will all play out. The success of Catfish spawned a television show by the same name on MTV.
From this one story, we can easily see the problems that can arise from anonymity on the Internet. Often behavior that would be deemed completely inappropriate in a face to face encounter suddenly becomes appropriate because it’s deemed “less real” by some. One of the major problems with online anonymity has been cyberbullying. People today can post horrible things about one another online without any worry that the messages will be linked back to them directly. Unlike face to face bullying victims who leave the bullying behind when they leave school, teens facing cyberbullying cannot even find peace at home because the Internet follows them everywhere. In 2013 12-year-old Rebecca Ann Sedwick committed suicide after being the perpetual victim of cyberbullying through social media apps on her phone. Rebecca suffered a barrage of bullying for over a year and by around 15 different girls in her school. Sadly, Rebecca’s tale is one that is all too familiar in today’s world. Nine percent of middle-school students reported being victims of cyberbullying, and there is a relationship between victimization and suicidal ideation.
It’s also important to understand that cyberbullying isn’t just a phenomenon that happens with children. A 2009 survey of Australian Manufacturing Workers’ Union members, found that 34% of respondents faced FtF bullying, and 10.7% faced cyberbullying. All of the individuals who were targets of cyberbullying were also bullied FtF.51
Many people prefer anonymity when interacting with others online, and there can be legitimate reasons to engage in online interactions with others. For example, when one of our authors was coming out as LGBTQIA+, our coauthor regularly talked with people online as they melded the new LGBTQIA+ identity with their Southern and Christian identities. Having the ability to talk anonymously with others allowed our coauthor to gradually come out by forming anonymous relationships with others dealing with the same issues.
Pseudonymous Identity
The second category of interaction is pseudonymous. Wood and Smith used the term pseudonymous because of the prefix “pseudonym”: “Pseudonym comes from the Latin words for ‘false’ and ‘name,’ and it provides an audience with the ability to attribute statements and actions to a common source [emphasis in original].”52 Whereas an anonym allows someone to be completely anonymous, a pseudonym “allows one to contribute to the fashioning of one’s own image.”53 Using pseudonyms is hardly something new. Famed mystery author Agatha Christi wrote over 66 detective novels, but still published six romance novels using the pseudonym Mary Westmacott. Bestselling science fiction author Michael Crichton (of Jurassic Park fame), wrote under three different pseudonyms (John Lange, Jeffery Hudson, and Michael Douglas) when he was in medical school.
Even J. K. Rowling (of Harry Potter fame) used the pseudonym Robert Galbraith to write her follow-up novel to the series, The Cuckoo’s Calling (2013). Rowling didn’t want the media hype or inflated reader expectations while writing her follow-up novel. Unfortunately for Rowling, the secret didn’t stay hidden very long.
The veneer of the Internet allows us to determine how much of an identity we wish to front in online presentations. These images can range from a vague silhouette to a detailed snapshot. Whatever the degree of identity presented, however, it appears that control and empowerment are benefits for users of these communication technologies.”54
Some people even adopt a pseudonym because their online actions may not be “on-brand” for their day-job or because they don’t want to be fully exposed online.
Real Life Identity
Lastly, some people have their real-life identities displayed online. You can find people on Facebook, Instagram, Snapchat, Twitter, LinkedIn, etc…. Some realize that this behavior is a part of their professional persona, so they don’t put anything on one of these sites they wouldn’t want other professionals to see and read. When it comes to people in the public eye, most of them use some variation of their real names to enhance their brands. That’s not to say that many of these same people don’t have multiple online accounts, some of which may be completely anonymous or even pseudonymous.
Nonverbal Cues
One issue related to CMC is nonverbal communication. Historically, most of the media people have used to interact with one another have been asynchronous and text-based, making it difficult to fully ascertain the meaning behind a string of words. Mary J. Culnan and M. Lynne Markus believe that the functions nonverbal behaviors meet in interpersonal interactions simply go unmet in CMC (1987). If so, interpersonal communication must always be inherently impersonal when it’s conducted using computer-mediated technologies. This perspective has three underlying assumptions:
- Communication mediated by technology filters out communicative cues found in face to face interaction,
- Different media filter out or transmit different cues, and
- Substituting technology-mediated for face to face communication will result in predictable changes in intrapersonal and interpersonal variables.
First, CMC interactions “filter out” communicative cues found in face to face interactions. For example, if you’re on the telephone with someone, you can’t make eye contact or see their gestures, facial expressions, etc.… If you’re reading an email, you have no nonverbal information to help you interpret the message because there is none. In these examples, the nonverbal cues have been “filtered out” by the media being used.
Unfortunately, even if we don’t have the nonverbals to help us interpret a message, we interpret the message using our perception of how the sender intended us to understand this message, which is often wrong. How many times have you seen an incorrectly read text or email start a conflict? Of course, one of the first attempts to recover some sense of nonverbal meaning was the emoticon that we discussed earlier in this chapter.
One early realization about email and message boards was that people relied solely on text to interpret messages, which lacked nonverbal cues to aid in interpretation. On September 19, 1982, Scott Fahlman, a research professor of computer science at Carnegie Mellon, came up with an idea. You see, at Carnegie Mellon in the early 1980s (like most research universities at the time), they had their own bulletin board system (BBS), which discussed everything from campus politics to science fiction. As Fahlman noted,
“Given the nature of the community, a good many of the posts were humorous, or at least attempted humor.” But “The problem was that if someone made a sarcastic remark, a few readers would fail to get the joke and each of them would post a lengthy diatribe in response.”4

After giving some thought to the problem, he posted the message seen in Figure 12.3. Thus, the emoticon (emotion icon) was born. An emoticon is a series of characters that are designed to help readers interpret a writer’s intended tone or the feelings the writer intended to convey. Over the years, many different emoticons were created like the smiley and sad faces, lol (laughing out loud), ROFL (rolling on the floor laughing), :-O (surprise), :-* (kiss), 😛 (sticking your tongue out), :-/ (quizzical), :-X (sealed lips), 0:-) (angel), *\0/* (cheerleader), and so many others. As we’ve discussed previously in this text, so much of how we understand each other is based on our nonverbal behaviors, so these emoticons were an attempt to bring a lost part of the human communicative experience to a text-based communicative experience. These emoticons developed into emojis which have developed into apps like Bitmoji that allow for custom characters.
Key Takeaways
- CMC has changed throughout the years to allow for more interaction and communication online.
- Synchronous and asynchronous communication allows for different methods of communication.
- Following netiquette rules can help us to be more effective with our online communication.
- We use online platforms to create identifies for ourselves in the online environment.
- Nonverbal cues are typically missing from online interactions.
References
1 Holland, B. (2018, August 22). Human computers: The women of NASA. The History Channel. https://www.history.com/news/human-computers-women-at-nasa
2 Campbell-Kelly, Aspray, W., Ensbenger, N., & Yost, J. R. (2014). Computer: A history of the information machine (3rd ed.). Westview Press. Frauenfelder, M. (2013). The computer: an illustrated history from its origins to the present day. Carlton.
Garfinkle, S. L., & Grunspan, R. H. (2018). The computer book: From the abacus to artificial intelligence, 250 milestones in the history of computer science. Sterling.
3 Raz, G. (2019, October 29). ‘Lo’ and behold: A communication revolution. National Public Radio. https://www.npr.org/templates/story/story.php?storyId=114280698
4 Happy 25th, Emoticon. (2007, Summer). Carnegie Mellon University. Retrieved from https://www.cmu.edu/homepage/beyond/2007/summer/happy-25th-emoticon.shtml; para. 5.
5 Berners-Lee, T. (1990, May). Information management: A proposal. Retrieved from http://cds.cern.ch/record/369245/files/dd-89-001.pdf; pg. 3.
6 Ibid.; pg. 3.
7 Berners-Lee, T., & Cailliau, R. (1990, November 12). WorldWideWeb: A proposal for a HyperText project. Retrieved from http://cds.cern.ch/record/2639699/files/Proposal_Nov-1990.pdf
8 What is HTML5? (2013, December 12). Retrieved from https://www.w3.org/html/wiki/FAQs
9 Culnan, M. J., & Markus, M. L. (1987). Information technologies. In F. M. Jablin, L. L. Putman, K. H. Roberts, and L. W. Porter (Eds.), Handbook of organizational communication: An interdisciplinary perspective (pp.420-443). Sage.
10 Culnan, M. J., & Markus, M. L. (1987). Information technologies. In F. M. Jablin, L. L. Putman, K. H. Roberts, and L. W. Porter (Eds.), Handbook of organizational communication: An interdisciplinary perspective (pp.420-443). Sage; pg. 423.
11 Twitter. (n.d.). Hateful conduct policy. Retrieved from: https://help.twitter.com/en/rules-and-policies/hateful-conduct-policy
12 Decot, D. (1984, March 13). ***Asterisks***. Retrieved from: https://groups.google.com/forum/#%21msg/net.flame/VbghoeOfwyI/E2mClWj2GV8J
13 Brown, K. W., & Ryan, R. M. (2003). The benefits of being present: Mindfulness and its role in psychological well-being. Journal of Personality and Social Psychology, 84(2), 822–848. https://doi.org/10.1037/0022-3514.84.4.822
14 Abblett, M. (2019, September 3). 5 rules for sharing genuinely and safely online: No matter what kind of social community you find yourself in, it is important to abide by a few specific guidelines for safe sharing. Mindful.
15 Campbell, S. W., & Neer, M. R. (2001). The relationship of communication apprehension and interaction involvement to perceptions of computer-mediated communication. Communication Research Reports, 18(4), 391–398. https://doi.org/10.1080/08824090109384820
16 Ibid.; pgs. 396-397.
17 Spitzberg, B. H. (2006). Preliminary development of a model and measure of computer mediated communication (CMC) competence. Journal of Computer–Mediated Communication, 11(2), 629–666. https://doi.org/10.1111/j.1083-6101.2006.00030.x
18 Hunt, D., Atkin, D., & Krishnan, A. (2012). The influence of computer-mediated communication apprehension on motives for Facebook use. Journal of Broadcasting & Electronic Media, 56(2), 187–202. https://doi.org/10.1080/08838151.2012.678717
19 Punyanunt-Carter, N. M., De La Cruz, J. J., & Wrench, J. S. (2017). Investigating the relationships among college students’ satisfaction, addiction, needs, communication apprehension, motives, and uses & gratifications with Snapchat. Computers in Human Behavior, 75, 870–875. https://doi.org/10.1016/j.chb.2017.06.034
20 Punyanunt-Carter, N. M., Cruz, J. J. D. L., & Wrench, J. S. (2018). Analyzing college students’ social media communication apprehension. CyberPsychology, Behavior & Social Networking, 21(8), 511–515. https://doi.org/10.1089/cyber.2018.0098
21 CareerBuilder.com. (2018, August 9). More than half of employers have found content on social media that caused them NOT to hire a candidate, according to recent CareerBuilder survey [Press Release]. Retrieved from: http://press.careerbuilder.com/2018-08-09-More-Than-Half-of-Employers-Have-Found-Content-on-Social-Media-That-Caused-Them-NOT-to-Hire-a-Candidate-According-to-Recent-CareerBuilder-Survey
22 Ibid.
23 Ibid.; para. 6.
24 Ibid.; para. 7.
25 obVite (2013). 2013 social recruiting survey results. San Mateo, CA: Author.
26 Pitcan, M., Marwick, A. E., & Boyd, d. (2018). Performing a vanilla self: Respectability politics, social class, and the digital world. Journal of Computer-Mediated Communication, 23(3), 163-179. https://doi.org/10.1093/jcmc/zmy008; pg. 170.
27 Olsson, T., Jarusriboonchai, P., Woźniak, P., Paasovaara, S., Väänänen, K., & Lucero, A. (2019, February 14). Technologies for enhancing collocated social interaction: Review of design solutions and approaches. Computer Supported Cooperative Work. https://doi.org/10.1007/s10606-019-09345-0; pg. 2
28 Hewlett-Packard (2005). Abuse of technology can reduce UK workers’ intelligence. Small & Medium Business press release, April 22. Retrieved July 11, 2014, from http://www.scribd.com/doc/6910385/Abuse-of-technology-can-reduce-UK-workers-intelligence
29 Carrier, L. M., Cheever, N. A., Rosena, L. D., Benitez, S., & Chang, J. (2009). Multitasking across generations: Multitasking choices and difficulty ratings in three generations of Americans. Computers in Human Behavior, 25(2), 483-489. https://doi.org/10.1016/j.chb.2008.10.012
30 Bowman, J. M., & Pace, R. C. (2014). Dual-tasking effects on outcomes of mobile communication technologies. Communication Research Reports, 31(2), 221-231. https://doi.org/10.1080/08824096.2014.907149
31 Ibid.; pg. 228.
32 Olsson, T., Jarusriboonchai, P., Woźniak, P., Paasovaara, S., Väänänen, K., & Lucero, A. (2019, February 14). Technologies for enhancing collocated social interaction: Review of design solutions and approaches. Computer Supported Cooperative Work. https://doi.org/10.1007/s10606-019-09345-0
33 Ibid.; pg. 39
34 Ibid.; pg. 39
35 Ibid.; pg. 40
36 Ibid.; pg. 40
37 Erikson, E. H. (1968). Identity: Youth and crisis. W. W. Norton & Company.
38 Erikson, E. (1985). Pseudospeciation in the nuclear age. Political Psychology, 6(2), 213–217. https://doi.org/10.2307/3790901
39 Erikson, E. H. (1962). Reality and actuality an address. Journal of The American Psychoanalytic Association, 10(3), 451-474. https://doi.org/10.1177/000306516201000301
40 Erikson, E. H. (1988). Youth: Fidelity and diversity. Daedalus, 117(3), 1–24.
41 Ibid.; pg. 11.
42 Kay, A. (2018). Erikson Online: Identity and pseudospeciation in the Internet age. Identity: An International Journal of Theory and Research, 18(4), 264-273. https://doi.org/10.1080/15283488.2018.1523732; pg. 269.
43 Erikson, E. (1964). Insight and responsibility. Norton; pg. 103-104.
44 Goffman, E, (1959). The presentation of self in everyday life. Anchor Books.
45 Alfarid Hussain, S. M. (2015). Presentation of self among social media users in Assam: Appropriating
Goffman to Facebook users’ engagement with online communities. Global Media Journal: Indian Edition, 6(1&2), 1–14. https://tinyurl.com/sbbll8a
46 Alfarid Hussain, S. M. (2015). Presentation of self among social media users in Assam: Appropriating Goffman to Facebook users’ engagement with online communities. Global Media Journal: Indian Edition, 6(1&2), 1–14. https://tinyurl.com/sbbll8a; pg. 3.
47 Bullingham, L., & Vasconcelos, A. C. (2013). “The presentation of self in the online world:” Goffman and the study of online identities. Journal of Information Science, 39(1), 101–112. https://doi.org/10.1177/0165551512470051; pg. 110.
48 Ibid.; pg. 110.
49 Wood, A. F., & Smith, M. J. (2005). Online communication: Linking technology, identity, & culture (2nd ed.). Routledge.
50 Hinduja, S., & Patchin, J. W. (2010). Bullying, cyberbullying, and suicide. Archives of Suicide Research, 14, 206-221.
51 Privitera, C. (2009). Cyberbullying: The new face of workplace bullying? Cyberpsychology & Behavior, 12(4), 395-400. https://doi.org/10.1089/cpb.2009.0025
52 Wood, A. F., & Smith, M. J. (2005). Online communication: Linking technology, identity, & culture (2nd ed.).
Routledge; pg. 64.
53 Ibid.; pg. 66.
54 Ibid.; pgs. 66-67.
55 Katz, E., Blumler, J. G., & Gurevitch, M. (1974). Utilization of mass communication by the individual. In J. G. Blumler, & E. Katz (Eds.), The uses of mass communications: Current perspectives on gratifications research (pp. 19-32).: Sage.
56 Papacharissi, Z. & Rubin, A. M. (2000). Predictors of Internet use. Journal of Broadcasting & Electronic Media, 44(2), 175–196. https://doi.org/10.1207/s15506878jobem4402_2
57 Pornsakulvanich, V., Haridakis, P., & Rubin, A. M. (2008). The influence of dispositions and Internet motivation on online communication satisfaction and relationship closeness. Computers in Human Behavior, 24(5), 2292–2310. https://doi.org/10.1016/j.chb.2007.11.003
58 Short, J. A., Williams, E., & Christie, B. (1976). The social psychology of telecommunications. Wiley.
59 Lee, K.-M., & Nass, C. (2005). Social-psychological origins of feelings of presence: Creating social presence with machine-generated voices. Media Psychology, 7(1), 31-45. https://doi.org/10.1207/S1532785XMEP0701_2
60 Krupić, D., Žuro, B., & Corr, P. J. (in press). Anxiety and threat magnification in subjective and physiological responses of fear of heights induced by virtual reality. Personality and Individual Differences. https://doi.org/10.1016/j.paid.2019.109720
61 Wood, A. F., & Smith, M. J. (2005). Online communication: Linking technology, identity, & culture (2nd ed.). Routledge; pg. 72.
62 Wrench, J. S., & Punyanunt-Carter, N. M. (2007). The relationship between computer-mediated-communication competence, apprehension, self-efficacy, perceived confidence, and social presence. Southern Journal of Communication, 72(4), 355-378. https://doi.org/10.1080/10417940701667696
63 Daft, R. L., & Lengel, R. H. (1983, May). Information richness: A new approach to managerial behavior and organization design (Report no. TR-ONR-DG-02). Office of Naval Research.
64 Ibid.; pg. 7.
65 Lengel, R. H. (1983). Managerial information process and communication-media source selection behavior [Unpublished Doctoral Dissertation]. Texas A&M University.
66 D’Ambra, J. D., Rice, R. E., & O’Conner, M. (1998). Computer-mediated communication and media preference: An investigation of the dimensionality of perceived task equivocality and media richness. Behaviour and Information Technology, 17(3), 164-174. https://doi.org/10.1080/014492998119535
67 Walther, J. B. (1992). Interpersonal effects in computer-mediated interaction: A relational perspective. Communication Research, 19(1), 52–90. https://doi.org/10.1177/009365092019001003
68 Walther, J. B. (1996). Computer-mediated communication: Impersonal, interpersonal, and hyperpersonal interaction. Communication Research, 23(1), 3-43. https://doi.org/10.1177/009365096023001001

